In a windowless office in the Pasadena Police Department’s detective bureau, Det. Brian Murphy sits at his desk, surrounded by three computer screens.
Murphy is investigating a burglary case in which the suspect has photos of victims’ IDs, credit cards and other personal information stored on his cell phone, which he then planned to use in a variety of nefarious ways.
Using technology, Murphy will essentially search the phone in the same away investigators search a home or business for evidence of crimes, all centering around identity theft.
“It’s a burglary case but this guy was looking for people’s identities,” said Murphy whose been a cyber investigator for about a year. “My job is to go in and find that (evidence) and hand it over to (detectives). I’m here more to assist them if they need information off a digital device.”
Murphy went through 16 training classes totaling about 500 hours to gain the technical knowhow needed to gain access to electronic devices and retrieve information, even material that had been deleted long ago.
While Murphy is getting into devices as one of the good guys, there’s a population of bad guys who also want to get into electronic devices too.
When a burglar breaks into a home or business, stealing documents containing the victims’ social security or driver license numbers makes for a bigger score than heisting a TV.
The reason: stealing an identity enables a bad guy to acquire 20 TVs. Cyber criminals use personal information to create phony IDs and credit cards and charge up a storm on someone else’s’ credit.
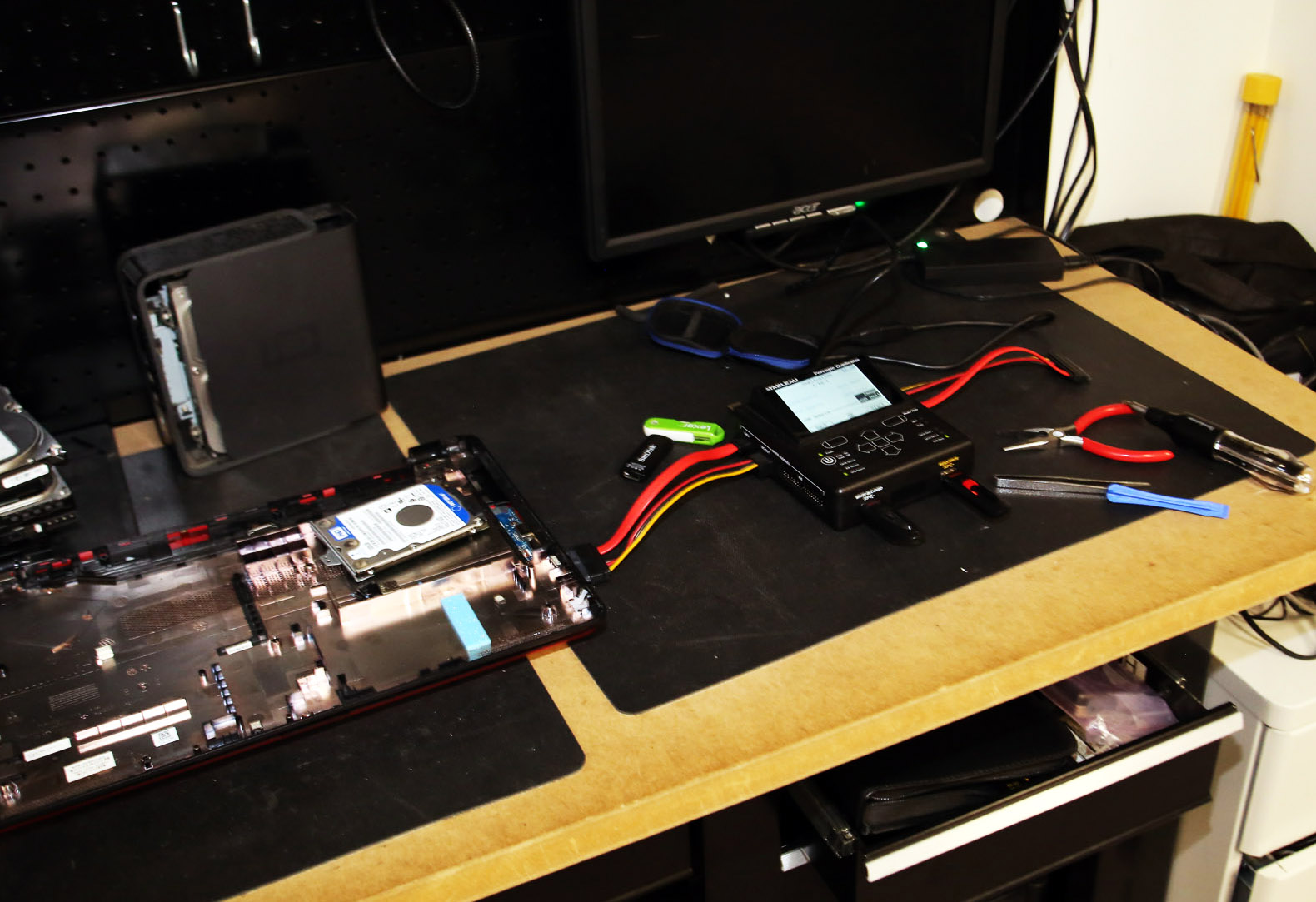
Investigating computer hard drives and components is part of the challenge working in the electric crimes unit. Photo by James Carbone
“If I was to break into your car, the first thing I would do after getting your credit card and wallet, is go to Apple and charge as much as I can,” said Property Crimes Det. Derrick Carter, on the job for 34 years. “They got your information, so they can basically open up accounts in your name and bust those out.”
Bad guys don’t even need to break into a house at all to steal. They can do it from anywhere.
One common method – phishing – involves sending fraudulent e-mails purported to be from a legitimate company, trying to get unsuspecting victims to reveal credit card numbers and passwords.
“A lot of these bad guys, they are engineering their attacks on people,” Carter said. “Just getting people to click and download something, and once they download it, they are into your system. There is somebody in there looking at all their stuff and they are oblivious to it. Next thing you know they are missing $,5000 from their account.”
In one recent case, Pasadena PD took down an identity theft ring operating out of a local hotel room.
Investigators found 199 credit cards, Carter said. Many were produced with identifies of victims in China, Russia and South America, who may have had their IDs stolen in the U.S.
The same crew was renting cars and buying merchandise using the phony cards.
“It was a big operation,” Carter said.
Social networking accounts, often packed with personal information, are also favorite targets of hackers, Carter said.
In larger scale cases, Pasadena PD partners with the Secret Service or the Department of Homeland Security to catch the criminals, which may be operating from another country.
ID theft also takes place through “skimmers,” a device which is inserted into card readers in ATM machines.
When the unsuspecting victim slides their debit or credit card into the card reader, the skimmer reads the magnetic strip, or stripe, and stores the card holder’s name, card number and expiration date.

Derrick Carter from the Pasadena Police Detective for the Electronic Crimes and Financial Unit works at his desk at the Pasadena Police Department on February 21, 2019. Photo by James Carbone
Ultimately, the victims are the banks, Carter said.
Carter meets monthly with the California Financial Crimes Investigators Association, where bank fraud investigators and detectives who work financial crimes collaborate to enhance investigative skills.
To stay on equal footing with cyber criminals, Murphy goes through training to stay current with the constantly evolving technology.
Sometimes, they learn from the bad guys themselves.
“They’ll sit there and explain to you how they did it,” Carter said. “Some of them are proud of it.”
 Behind the Badge
Behind the Badge



